In our previous blog, we explored how Docker Scout helps improve image compliance and container security through policies, attestations, and vulnerability insights. Now, let’s take the next step—analyzing your image in the Docker Scout Dashboard and exploring integrations that supercharge your software supply chain visibility.
Note: This blog is the 4th and final part of our series on Docker Scout. To navigate directly to a specific section, please refer to the links below:
1st part link: Docker-Scout
2nd part link: Enablement and analysis of Docker Scout
3rd part link: Evaluate policy compliance& improve compliance of Docker Scout
After pushing the updated image, we can view the results through the Docker Scout Dashboard. what happens after you’ve pushed your image with attestations, and how to analyze compliance using the Docker Scout Dashboard.
lets explore:
1.Navigating the Docker Scout Dashboard
Docker Scout provides an intuitive web interface that displays the health, compliance, and security posture of your images. Here’s how to get started:
Open the Docker Scout Dashboard
- Navigate to:
https://docs.docker.com/scout→ click Dashboard - Or directly visit:
https://hub.docker.com/scout/dashboard - Sign in with your Docker ID
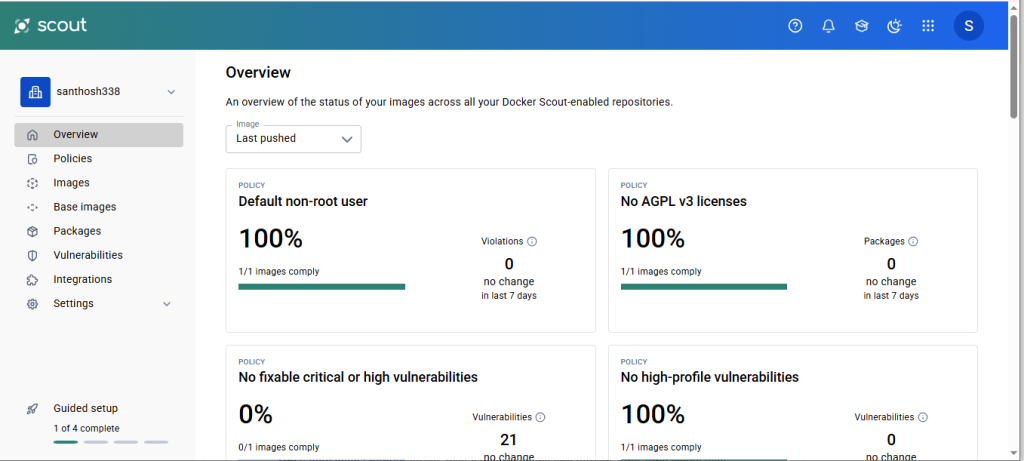
2. Navigate to Scout-enabled Repositories
- In the left-hand menu, click Images.
- You’ll see a list of repositories that are:
- Scout-enabled (i.e., contain images pushed with provenance and SBOM)
- Tagged and analyzed
3. Open Image Details Sidebar
- Click anywhere on the row (except links) for your pushed image, e.g., ORG_NAME/scout-demo.
- A sidebar will open showing:
- Compliance overview for the latest tag (e.g., v3)
- Policy violations (like Non-root, Base image, etc.)
- SBOM and attestation status
Tip: If data hasn’t populated yet, wait a minute or two and refresh. First-time scans take a bit longer.
4. Check Base Image Policy Compliance
- Go back to the image list and click the version shown under Most recent image.
- In the top right corner of the image details page, click Update base image.
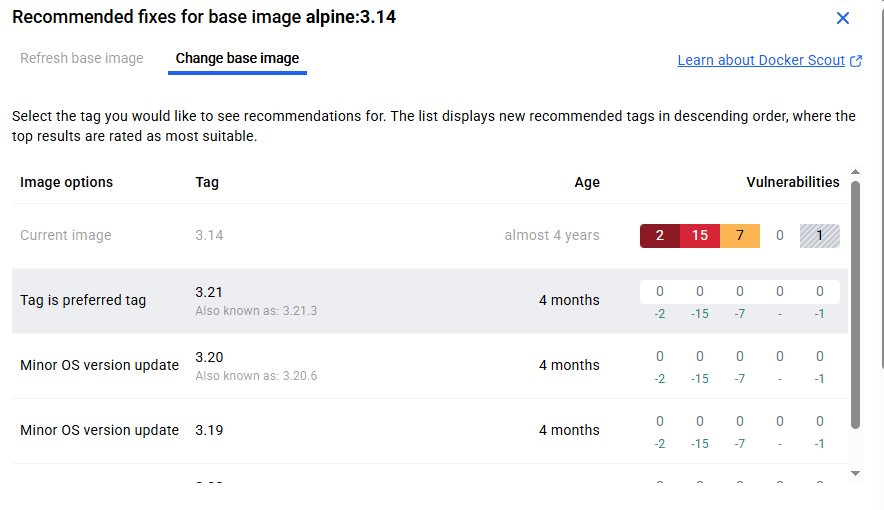
Why it’s non-compliant:
- image uses an older version of Alpine (e.g., alpine:3.14), which may contain:
- Known vulnerabilities
- End-of-life (EOL) status
- The base image policy is failing because you’re not using a recent or secure base image.
5. View Recommended Fixes
- Close the Update base image modal.
- In the list of policies, next to the failed base image policy, click View fixes.
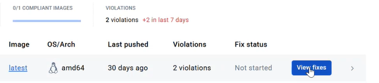
- This will show:
- Specific version recommendations (e.g., alpine:3.19)
- The exact Dockerfile line that needs to be updated
- Related CVEs that would be resolved
If you decide to follow Scout’s recommendation , you can proceed
Docker Scout Integrations: Supercharge Your Security Posture
Beyond analyzing Docker Hub images, Docker Scout offers a wide range of integrations across your software lifecycle. These help bring visibility into build pipelines, running environments, codebases, and more.
Container Registry Integrations
Analyze images stored outside Docker Hub.
Supported:
Scout retrieves metadata and analyzes images across cloud-native ecosystems.
Continuous Integration (CI) Integrations
Get instant feedback during your build process.
Supported CI tools:
- 1. GitHub Actions
- 2. GitLab
- 3. Microsoft Azure DevOps Pipelines
- 4. Circle CI
- 5. Jenkins
Enhance “shift-left” security by analyzing images and policies during your CI runs.
Environment Monitoring
Compare running workloads with your image repository data in real-time.
Available: Sysdig
Great for validating what’s deployed in production vs. what was built.
Code Quality Integrations
Apply quality gates directly to source code for early-stage security and quality assurance.
Available: SonarQube
Code quality insights appear alongside Docker Scout results for improved traceability.
Source Code Management (SCM)
Get remediation advice directly in your code repositories.
Supported: GitHub
Ideal for guiding developers through fixing base image or policy issues natively in the dev workflow.
Team Collaboration
Send real-time alerts to your team’s preferred communication platform.
Supported: Slack
Broadcast security and compliance updates to your team proactively
Conclusion: Secure Containers, the Docker Scout Way
In this four-part series, we walked through Docker Scout’s powerful capabilities — from setup and installation to policy enforcement and dashboard insights — helping you bring security, compliance, and visibility into every step of your container development workflow.
Whether you’re a developer pushing images, a DevOps engineer running pipelines, or a security lead managing policy compliance, Docker Scout seamlessly integrates into your tools, processes, and ecosystem.
To recap:
- In Part 1, we laid the foundation — installing Scout, authenticating Docker, and building your first secure image.
- In Part 2, we enabled Scout on repositories and scanned both local and remote images for known vulnerabilities using rich CVE insights.
- In Part 3, we enforced policy compliance and improved image hygiene by fixing violations and generating SBOMs and provenance data.
- In Part 4, we explored the Docker Scout Dashboard and key integrations that enhance visibility across registries, CI/CD, SCM, and runtime environments.
Bottom line: Docker Scout isn’t just a tool — it’s a shift-left security mindset, empowering teams to build, test, and ship secure containers by design, not by afterthought.
This wraps up the series on Docker Scout
You now have a complete picture of Docker Scout — from setup and scanning, to enforcing policies and managing security posture at scale.
